
Sign up for Prowler Updates
Introducing Prowler’s GitHub Provider: Secure Your Repositories at Scale
Recently we have seen a rise of incidents related to supply chain attacks, and specifically with the security of the development pipelines: tj-actions, reviewdog/action-setup, Amazon Q Developer, nx and others.
Pipelines have privileged access to your code, infrastructure, and secrets, making them a critical component of any modern software development lifecycle (SDLC). But, even though it is a fundamental piece, sometimes it is overlooked.
This isn’t just an open source problem, private repositories are also vulnerable to these risks. Not only because of insider attacks, but also because a misconfiguration could end up exposing your source code to the public.
In one of our Cloud Village workshops at Defcon, Level Up Your CI/CD: Building a secure pipeline with OSS, we talked about how to implement different open source tools to increase the security of your pipelines, and of course, one of them was Prowler.
A new Prowler provider: GitHub
As the most popular platform to host code, we wanted to start our pipeline security journey with GitHub. And the first stop is not the pipeline itself, but your Repository and Organizations settings, how can your pipeline be secure if your organization itself is vulnerable?
We made an initial release with 17 checks covering an important part of the CIS GitHub Benchmark, you can see the list in Prowler Hub.
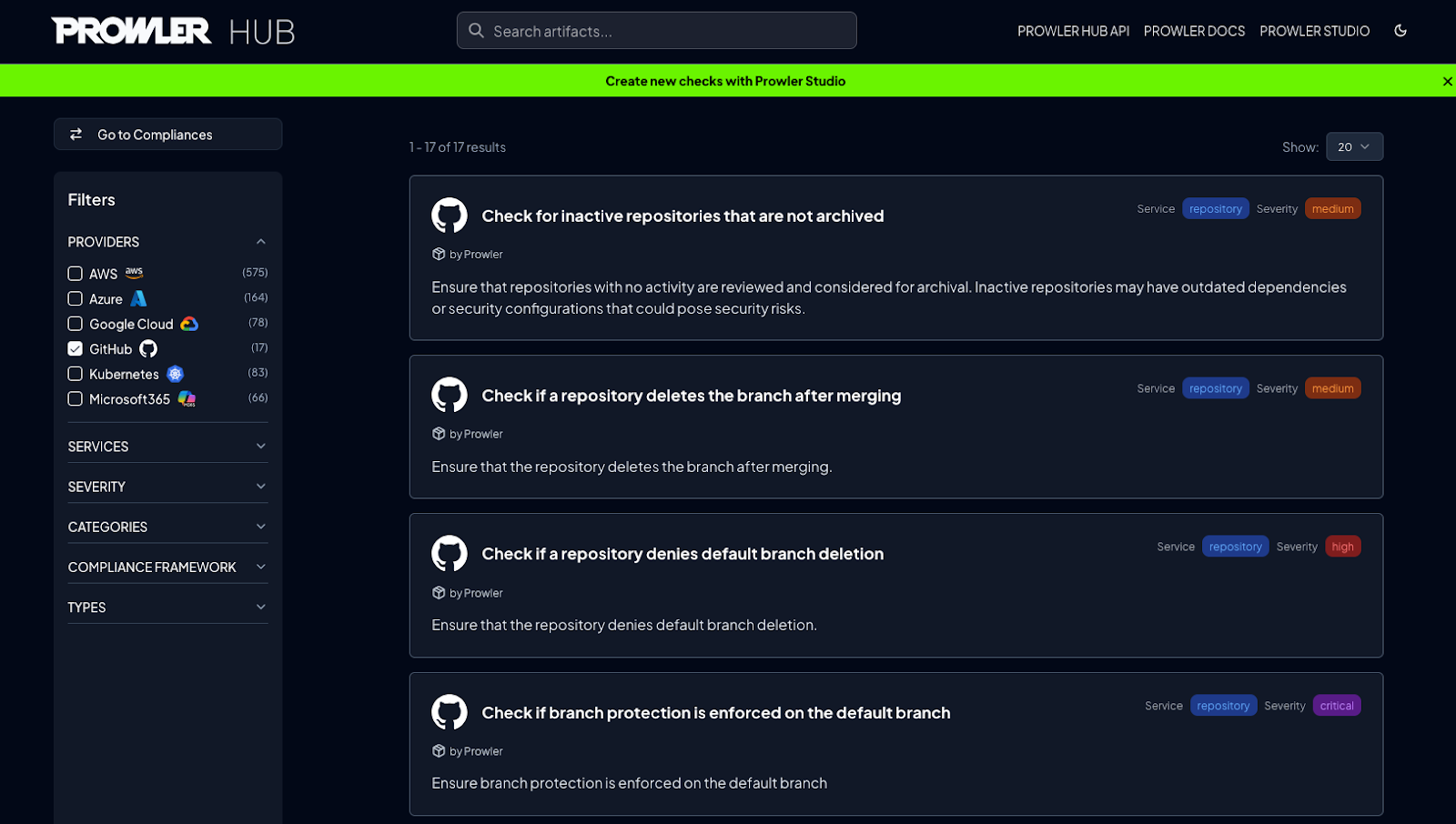
How to use it
Let’s do an experiment. How good are GitHub default settings? I just created a GitHub new account, with a new organization and a few repositories. Let’s run a Prowler scan and see the results.
If you prefer video, here’s a quick walkthrough of how GitHub provider works in just 2 minutes.
We support three authentication methods, if you’re going to scan only one account or organization, Personal Access Token is the easiest way to do it.
But, if you have several organizations, creating a GitHub App and installing it in the ones you want to scan can be a way to simplify the process.
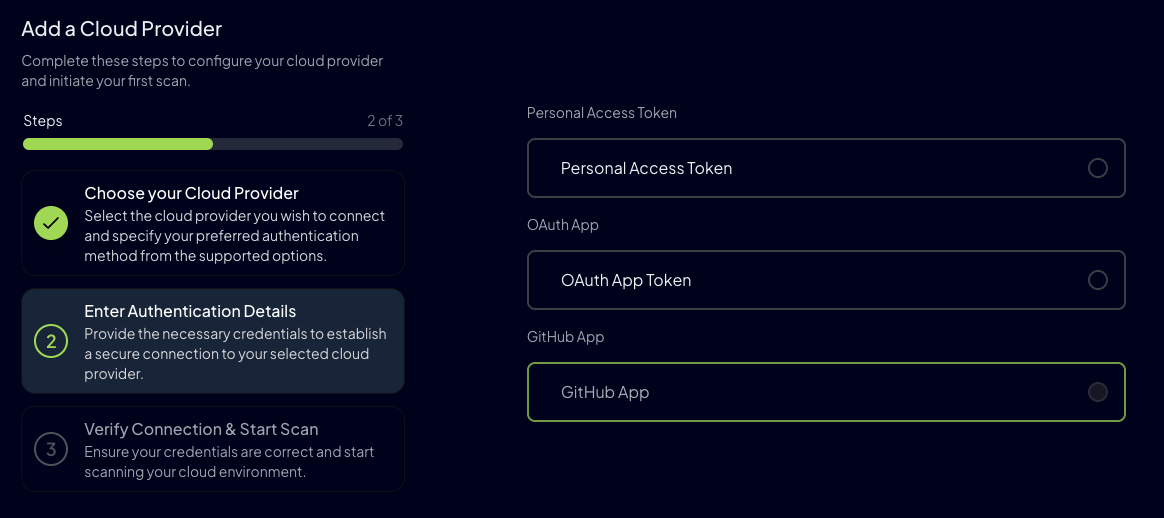
For this example we used PATs to add both the new user and the new organization:
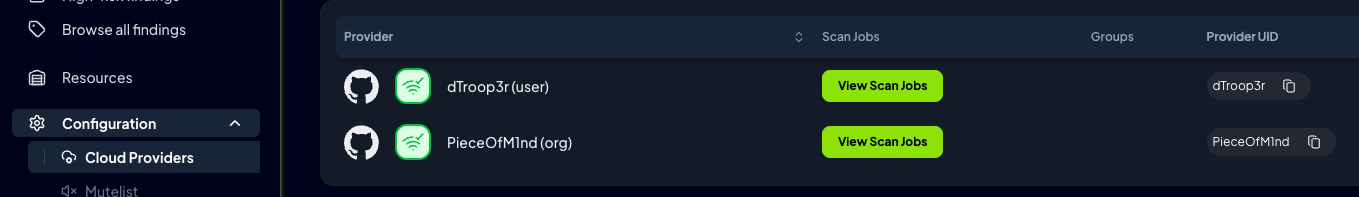
Once the scan finishes we can review the results, let’s start with the organization.
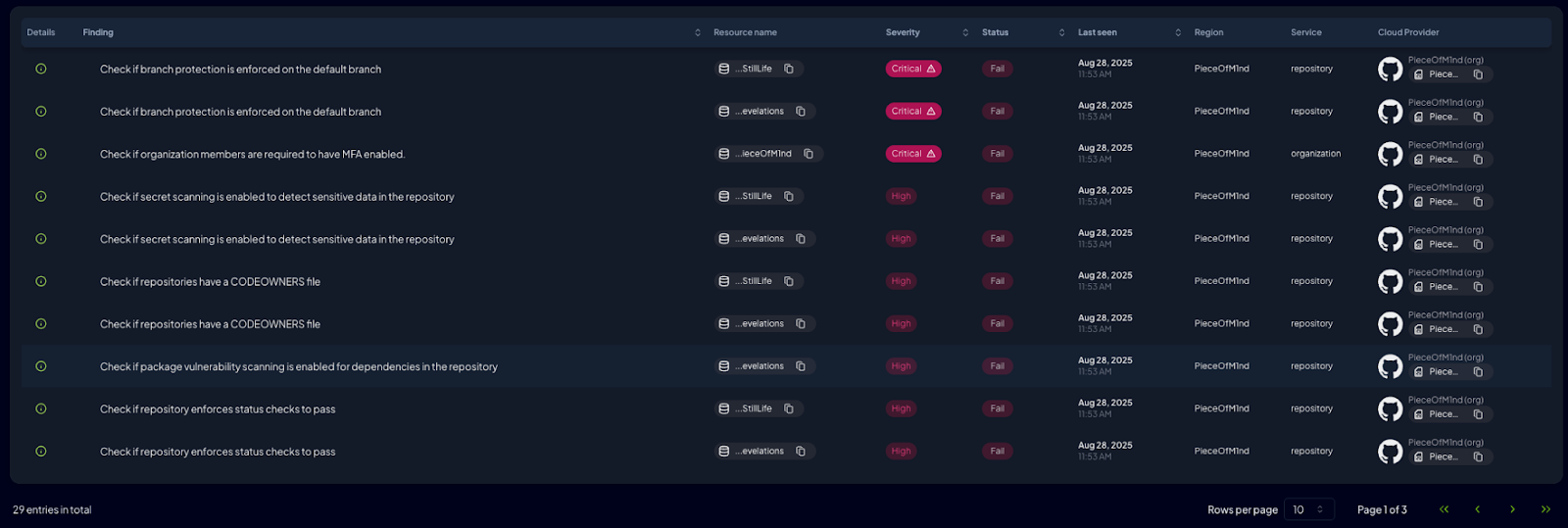
It found our 3 resources: the organization itself and the two repositories. And we have 29 findings, 3 of them critical!
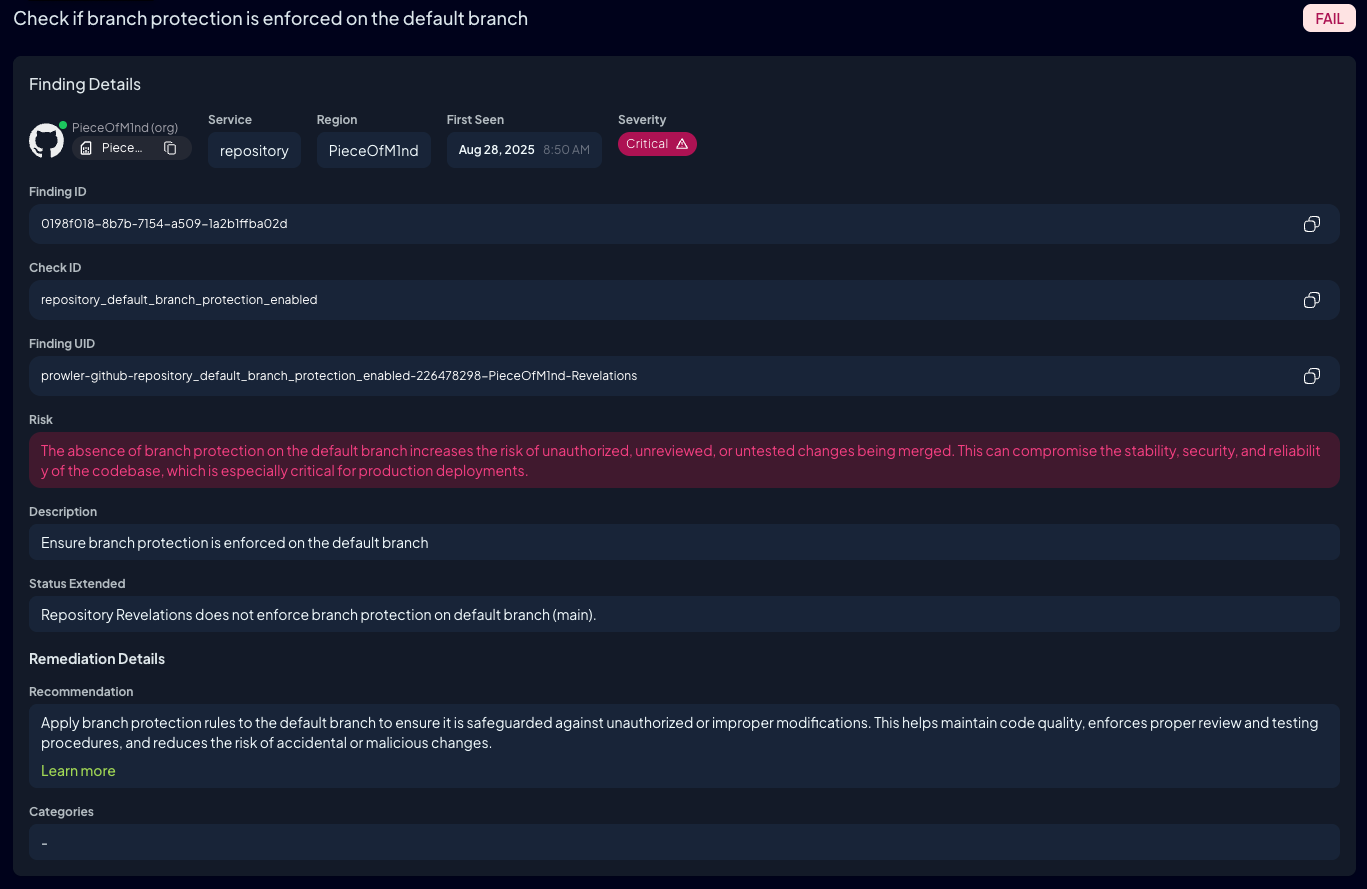
For both repositories, branch protection on the default branch is not enabled. Meaning that changes can be pushed directly to the main branch.
And for the organization, members are not being required to have MFA enabled.
Now we know that by default, these important security controls don’t come activated.
In the rest of the findings, a lot of them will depend on who manages the repositories: an individual, a very small team, a big organization… But I want to highlight these two, that for me, are always important:
- Check if a repository denies default branch deletion: You probably don’t want anyone deleting your main branch, not even you by mistake.
- Check if secret scanning is enabled to detect sensitive data in the repository: Mistakes happen, you should never commit your secrets, but if it happens, you want to be aware as soon as possible.
Conclusion
Default settings prioritize usability over security, which isn’t inherently bad, but it means organizations need to actively harden their configurations. Our experiment with a fresh GitHub account revealed that even basic security controls like branch protection and MFA aren’t enabled by default.
Now using Prowler you can quickly see which settings you need to improve your GitHub security posture. And you can do it with natural language leveraging Lighthouse AI, our security assistant.
Just ask “What GitHub security issues should I prioritize?” and get actionable recommendations.
Secure Your GitHub Environment with Prowler Cloud
Ready to see what security gaps exist in your GitHub organization? Prowler Cloud provides automated, continuous security assessments for GitHub, AWS, Azure, GCP, M365 and Kubernetes.
Don’t wait for a supply chain attack to discover your vulnerabilities.
Stay secure 🤘
Recent Articles

Automate Multi-Cloud Security at Scale: Bulk Provider Provisioning in Prowler
Managing cloud security across dozens or even hundreds of cloud accounts is a challenge, especially when you have to do it for multiple cloud providers. Manually onboarding each account is...

Unmasking Hidden Dangers: How Prowler Now Detects Obfuscated IAM Policies
It all started with a fascinating blog post from the team at Permiso introducing their "Sky Scalpel" tool. Their research highlighted a clever technique for hiding dangerous permissions within AWS...

Bedrock’s New API Keys: Convenience at a Hidden Security Cost
Recently, the AWS team rolled out the red carpet for a slick new feature in their post, "Accelerate AI development with Amazon Bedrock API keys." The promise was a dream...