Following breadcrumbs to code: A proof of concept.

A big part of the open cloud security movement is Transparency, so with that, lets tackle Prowler’s ability to use existing “Breadcrumbs” left by our cloud deployments to find it’s original Infrastructure-as-Code (IaC) without any hidden magic.
The concept is simple, can we make users’ lives easier by providing context back into their codebase from objects already deployed into their runtime environment?
First we’ll start by updating a couple of EC2 instances in my demo AWS environment. Any objects would work, the main difference is i’m practicing good tagging policy (like some of the best orgs out there) and auto-tagging my Terraform resources with Yor.io.
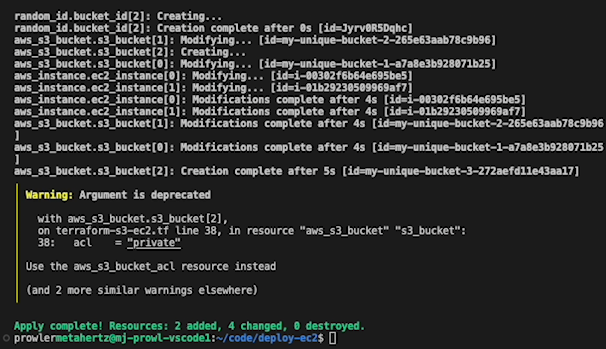
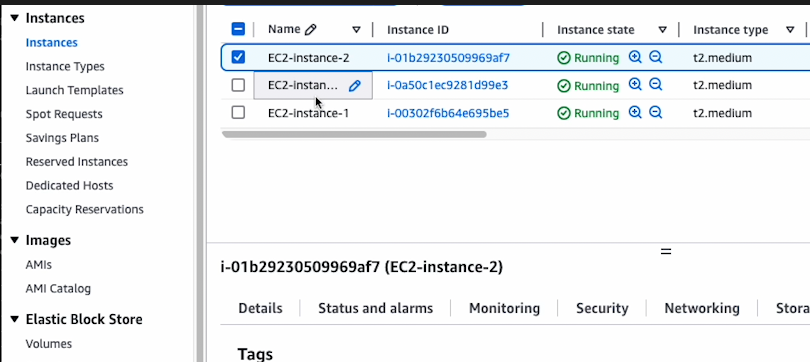
EC2 Instances updated, awesome!
However I’m guessing my terraform ChatGPT’s terraform may have been a little sloppy on the security side, we’re seeing prowler issues with our deployed cloud resources!
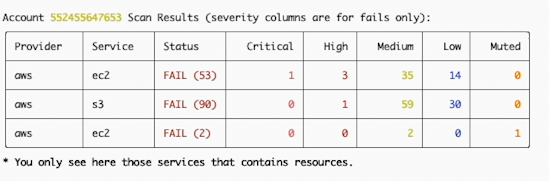
And again in pretty-fi prowler V5
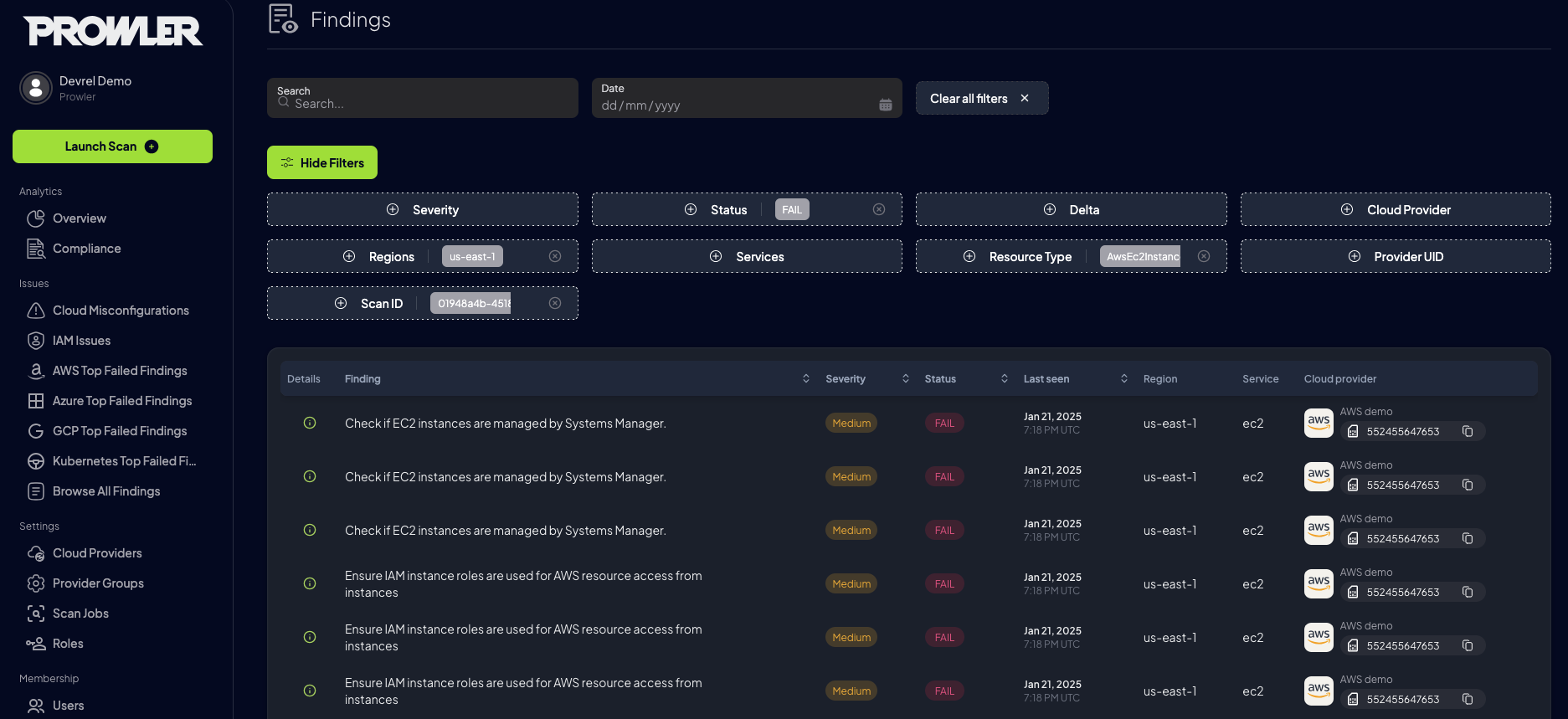
And the Results?
In this proof-of-concept, I’ve implimented the extra functionality as one of Prowlers’ “Output” formats. For feature-hackers, this offers one big advantage:
It’s a very easy way to add a new code path in the prowler codebase which gives access to all the results (findings dictionary) when activated.
In our case, we just add
--output-formats back2code
Simple enough! The downsides are that you are outside of the Prowler check/resource/provider threading system, so if you need to speed things up, you’ll have to implement threading yourself. Keep that in mind post-PoC if you’re looking to make new features for production in Prowler!
As well as our usual local HTML output format (–output-formats html) we now have a new .code.html file to browse!
In here we highlight any tags which we have located a git commit ID, and link back to github.com or gitlab.com if we have found that commit within either site:
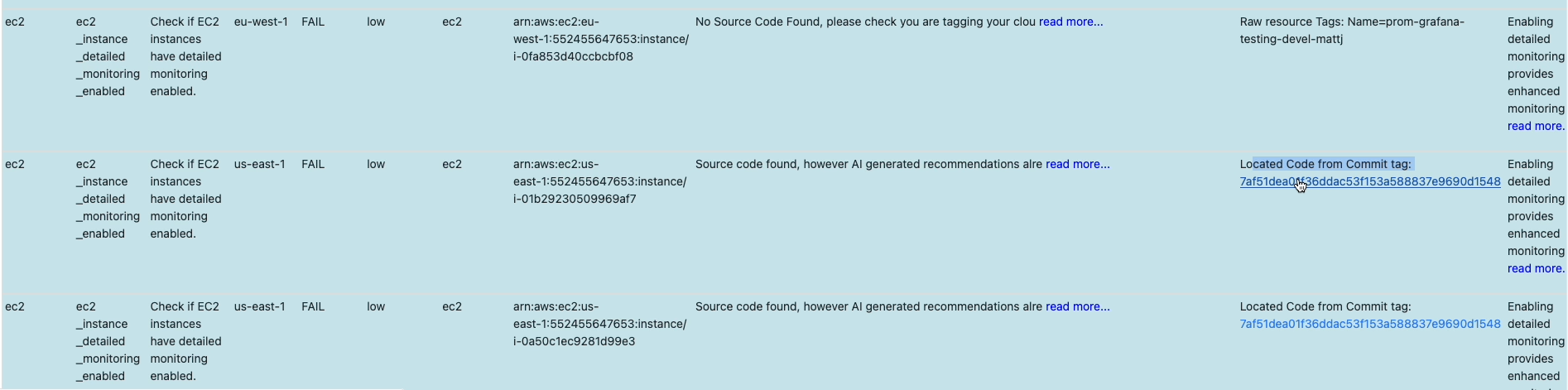
Clicking the link where available, takes you directly to the commit, in the repo that created your cloud resource:

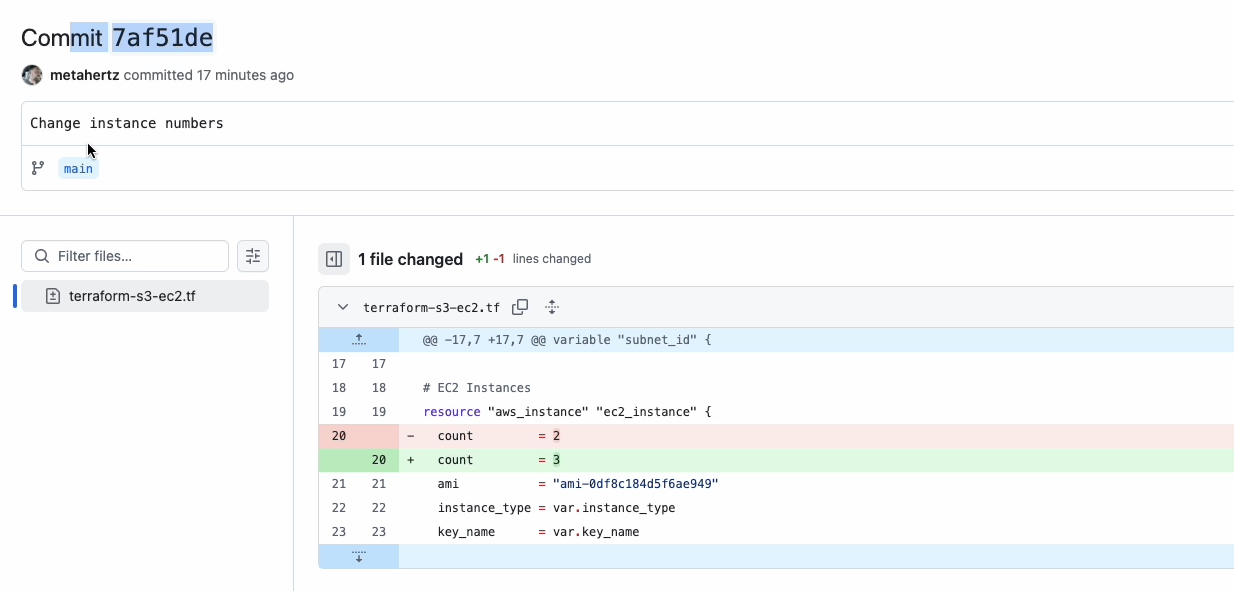
You can also provide your access token to the prowler instance (ie; GITHUB_TOKEN in my video example below) which would allow this to return results for private repositories your token has access too.
The many flavours of breadcrumb
Personally i’m a hearty Italian guy (yes, thats a Subway reference). But just like actual types of bread-crumbs, different cloud deployments will leave different traces, where this PoC just highlights one type of trace, a tagged cloud object, consider other marks left by default on our deployments:
- Helm Charts into a Kubernetes cluster leave their Chart name, version and other metadata as labels.
- CloudFormation deployments into AWS generally leave S3 assets behind from their template and also CloudTrail logs.
Did I hear you say AI?
While we’re already querying github.com and gitlab.com API’s for commit ID’s. We can pull down the file changed content from the located repo for our commit. We already have a description (from Prowler) of the security issue related to this code, so we can ask OpenAI to provide suggestions for a fix.
This part of the demo requires prowler to be supplied with a credited OpenAI token, as it’s using the O4 model. Our prompt provides the original code from the commit with instructions for markdown formatted terraform suggestions. With more “code completion specific” models hitting the market (i’m currently experimenting with Cursor.com for example) i’m excited to see where we could take these suggestions for different aspects of Prowlers output.
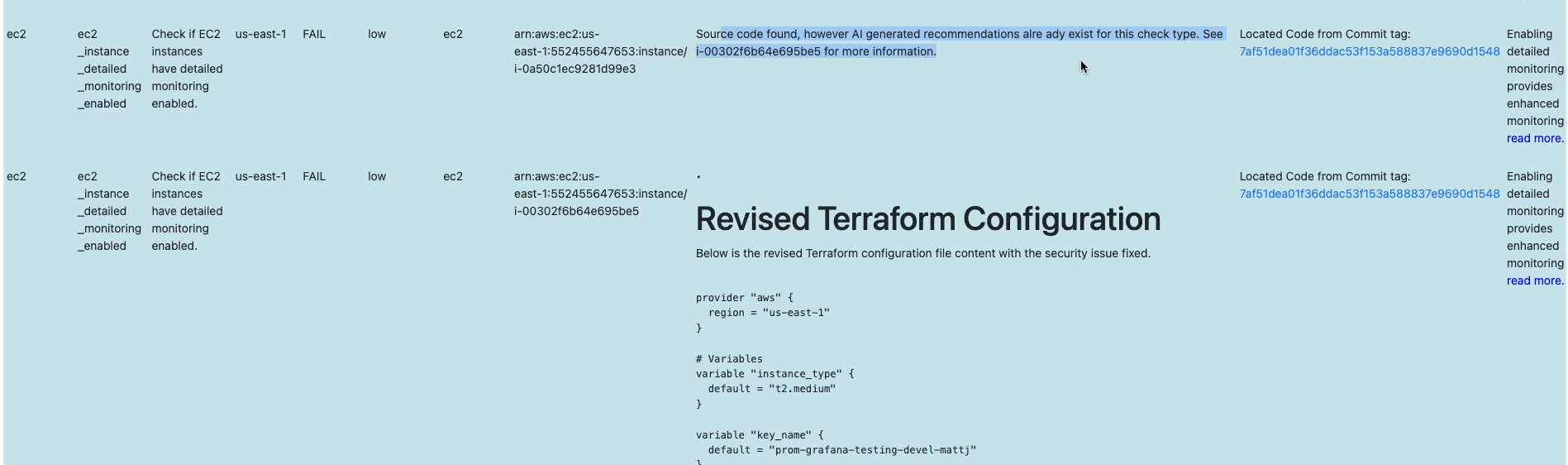
Next Steps
I’d love feedback for this “code search” feature and if it would benefit you as a user of Prowler!
I’ll be looking to extend the current capabilities with the Prowler engineering team as this turns from PoC code to a feature, ideally in the Prowler 5 UI! if you have any other suggestions for traceable runtime data, improvements, or ideas, please shout! You’ll find me in the #FeatureRequests channel in the Prowler slack: https://goto.prowler.com/slack
TL;DR, wheres my video?
Heres a video walkthrough of this in action!



.avif)

.avif)

