Adapting to Microsoft's MFA Enforcement: Prowler's New Certificate-Based M365 Authentication

The world of cloud security is constantly evolving, and staying ahead of the curve means adapting to new best practices and security measures. A few months ago, in version 5.3.0, we introduced Microsoft 365 support for the Prowler CLI, initially focusing on Service Principal authentication.
Soon after, we expanded this support, leveraging PowerShell modules for even broader coverage with username and password authentication. This combination allowed us to effectively tackle automated CIS controls for M365.
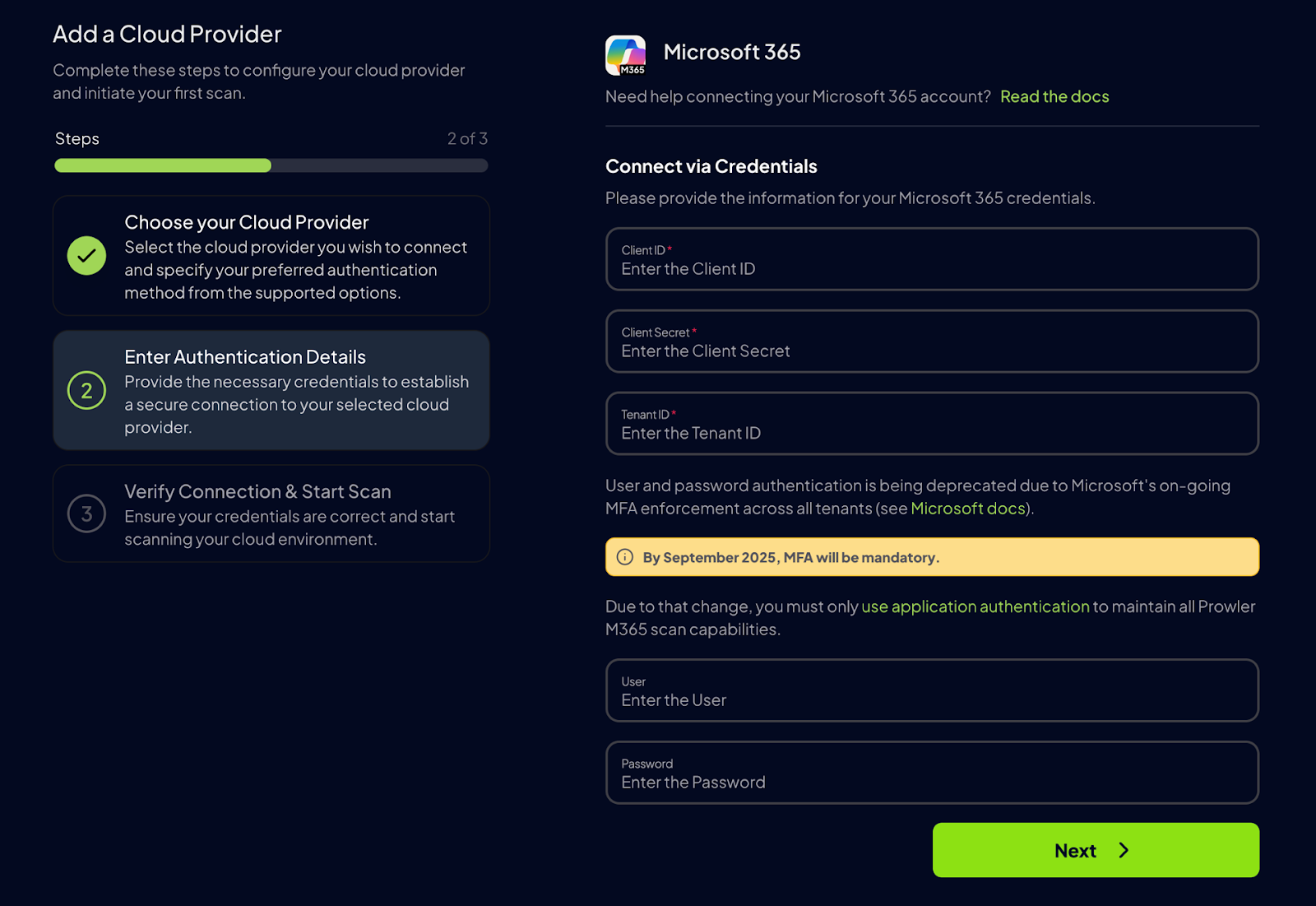
Then in August Microsoft announced they were going to move forward with their decision of enforcing MFA for delegated authentication (the one based on user credentials). This change effectively blocks non-interactive, programmatic access for this type of sign-in.

This measure is well justified, since Microsoft’s research shows that MFA prevents up to 99.22% of account compromise attempts, such as the password spraying attack reported by SecurityScorecard a few months ago. By requiring an additional verification step to ensure the legitimate account owner authorizes the access, attacks composed with password spoofing have become much less effective.
Nevertheless, this change directly affected us, as preventing executing M365 scans using the old user authentication method. To address this, we expanded support and implemented full Service Principal authentication, eliminating the need for user credentials.
After Microsoft fully enforced this policy and the user + password authentication became obsolete for programmatic access, we proceeded to deprecate that method. At the same time, we created a new alternative for Service Principal authentication without the need to use a Client Secret, the Certificate-based authentication.
With version 5.13, we’ve officially deprecated the user and password method and added this new certificate-based authentication method, which serves as a direct alternative to the client secret.
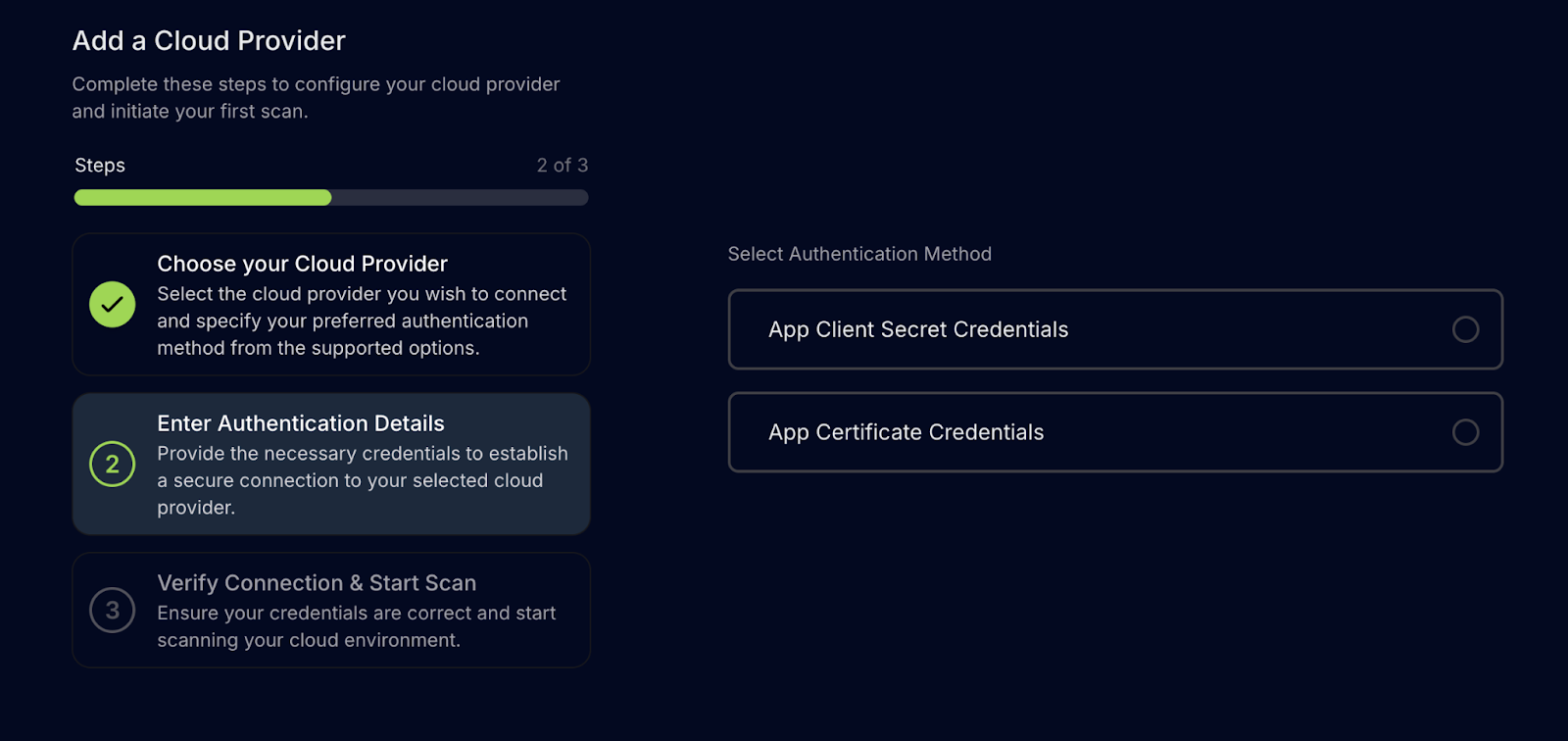
To use it, you can follow these steps:
- Create a self-signed certificate without a password.
- Upload the .cer certificate to your Microsoft Entra app.
- Generate a .pfx file from that certificate.
- Encode the .pfx file content in Base64.
- Provide the Base64-encoded content as a credential in Prowler Cloud to enable full M365 functionality.
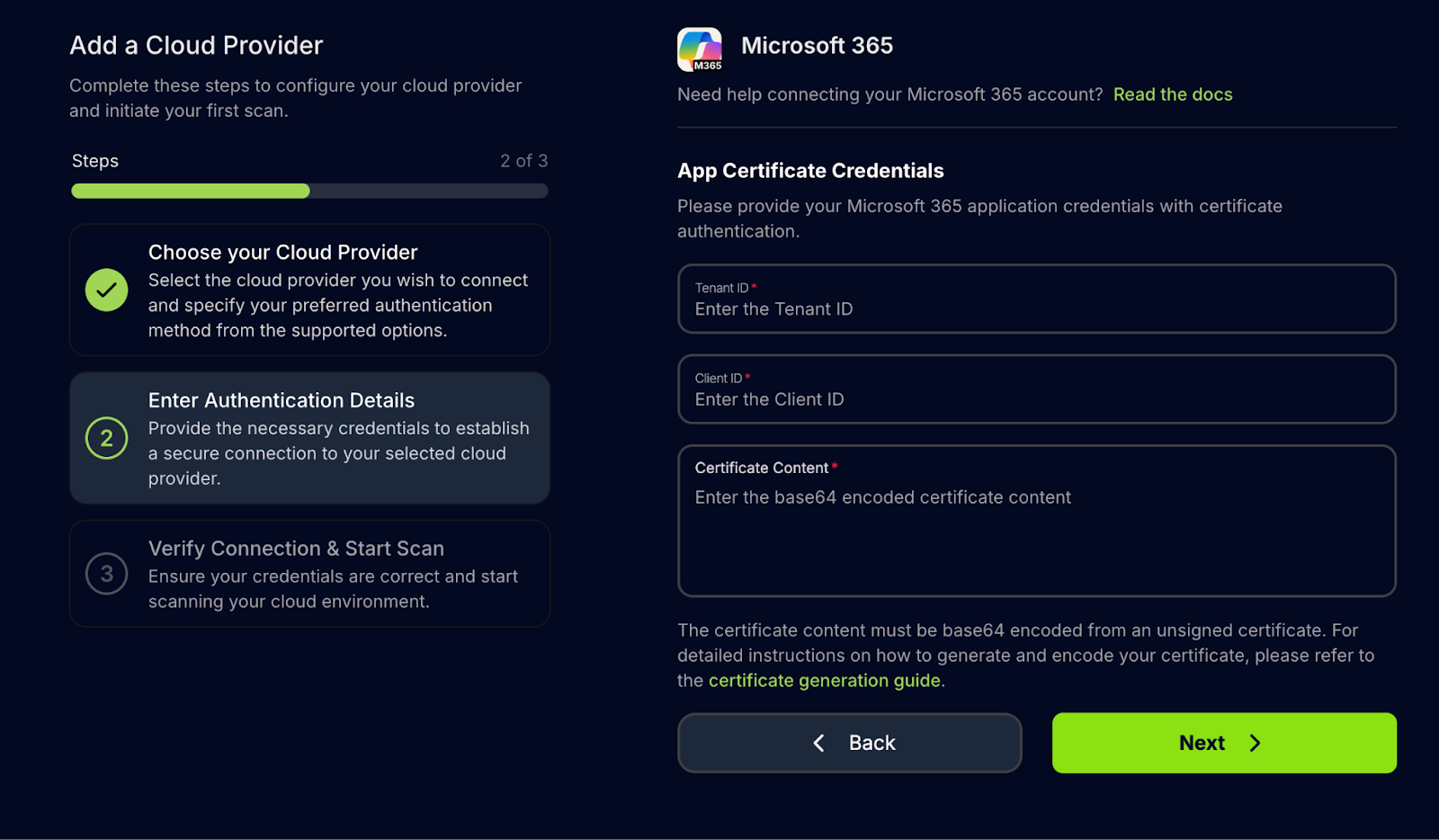
To see detailed steps on how to generate and configure the certificate, you can visit our documentation: Microsoft 365 Authentication - Generate the certificate
Ready to fortify your Microsoft 365 security with Prowler? Try it at cloud.prowler.com



.avif)

.avif)












