Finding What Really Matters: Introducing PDF Reports for Prowler ThreatScore

The Information Overload Problem
Cloud security has a weird problem. The better your tools get at finding issues, the harder it becomes to actually decide where to start.
Run a typical Prowler scan across your environment and you'll get hundreds, sometimes thousands of findings. Every single one is technically valid. But here's the thing: a publicly exposed S3 bucket with customer data is not the same as a missing tag on a dev server. Yet most reports dump everything on you with roughly the same urgency.
This creates a brutal choice: either spend hours manually sorting through findings to figure out what actually matters, or just pick something at random and hope you're working on the right thing. Neither option is great when you're trying to actually secure your infrastructure.
The problem isn't lack of information. It's too much of it, with no good way to figure out what demands your attention right now versus what can wait until next quarter.

The Solution: Smart PDF Reporting for ThreatScore
We built PDF reports for Prowler ThreatScore to solve exactly this problem.
After you run a scan, Prowler generates a PDF that cuts through the noise. Instead of listing every finding, it uses the ThreatScore framework to show you a risk-weighted view of what's actually happening in your environment.
The report evaluates each finding across four dimensions:
- Pass Rate - What percentage of checks passed for each requirement
- Total Findings - How much evidence backs up the assessment
- Weight (1-1000) - How important this requirement is to your organization
- Risk Level (1-5) - What happens if this requirement fails
The PDF organizes everything around ThreatScore's four pillars:
1. Identity and Access Management (IAM) This pillar controls who can access what in your environment and under what conditions. It breaks down into three key areas:
- Authentication - Verifying that users and systems are who they claim to be (MFA, password policies, service account security)
- Authorization - Controlling access to resources based on verified identity (least privilege, role-based access)
- Privilege Escalation - Preventing unauthorized elevation of permissions (admin account controls, excessive permissions)
2. Attack Surface This covers all the exposure points that attackers could exploit across your infrastructure:
- Network - Perimeter defense, network segmentation, firewall rules, VPC configurations, and traffic controls
- Storage - Database security, file system permissions, backup security, and storage encryption
- Application - Application security settings, code security, runtime protections, and input validation
3. Logging and Monitoring This ensures you have visibility into what's happening in your environment:
- Logging - Capturing security-relevant events and activities (audit trails, access logs)
- Retention - Maintaining logs for appropriate time periods for compliance and forensics
- Monitoring - Active surveillance and alerting on security events (real-time detection, incident response)
4. Encryption This protects your data confidentiality through cryptographic controls:
- In-Transit - Encrypting data during transmission (TLS/SSL, API encryption)
- At-Rest - Encrypting stored data (database encryption, volume encryption, object storage encryption)
Each pillar gets its own analysis in the PDF showing not just what failed, but why it matters and how much it affects your overall score.
Why ThreatScore Works
Most compliance scores are binary: pass or fail. ThreatScore actually understands context.
It knows that 100 failed checks for optional logging shouldn't matter more than 5 critical IAM failures. The framework uses a weighted formula that makes sure high-risk, high-weight requirements actually influence your score appropriately:
ThreatScore = (Σ (pass_rate × total_findings × weight × risk)) / (Σ (total_findings × weight × risk)) × 100
When you see a ThreatScore of 81.2% in your PDF, you're getting real information. The report breaks it down by pillar, so you can immediately see that your Encryption is solid at 94%, but your Attack Surface needs work at 77%.
Different organizations care about different things. A bank might set IAM controls to weight 950 with risk level 5, while giving Application controls weight 500 with risk 3. ThreatScore respects that, and your PDF reflects your actual priorities.
What This Looks Like In Practice
Say you just scanned your AWS production environment. You got 847 findings across 45 security checks. Looking at the raw output is overwhelming.
Your ThreatScore PDF opens with an overall score: 81.2%. Below that, you see:
- IAM: 87% (120 authorization control failures)
- Attack Surface: 77%
- Network: 80% (100 firewall config failures out of 400 checks)
- Storage: 75% (100 backup security failures out of 300 checks)
- Application: 75% (50 input validation failures out of 200 checks)
- Logging and Monitoring: 87%
- Encryption: 94%
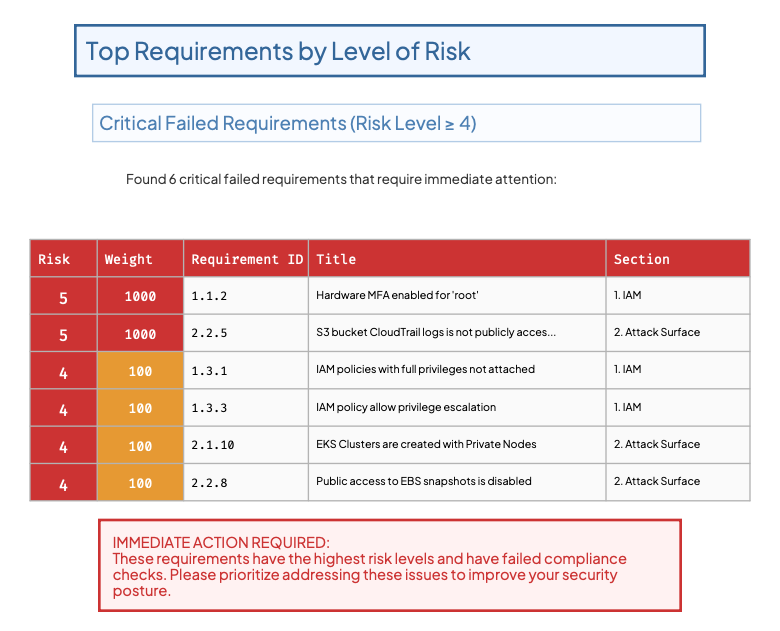
The report digs deeper. Those 100 firewall failures span 5 requirements, but one jumps out: "Public Endpoint Security" with weight 700 and risk level 4. That's where you start.
Compliance teams get normalized metrics that speak the language of risk. Security engineers get a prioritized work queue. Executives get a one-page summary that actually answers "are we secure?"

How It Works
The PDF generation runs asynchronously after your scan completes. The backend pushes your findings through the ThreatScore engine, aggregating results across requirements, subpillars, and pillars.
Edge cases are handled cleanly. Requirements with zero findings get excluded from calculations, so your score only reflects what was actually assessed.
The PDF includes visualizations of score trends, requirement-level breakdowns, and recommendations sorted by weighted risk impact. It's built to be shared with executives, auditors, and security teams who each need different things from the same data.
Get Started
The feature works now for AWS, Azure, GCP, and M365. After running your scan with Prowler, export the ThreatScore PDF to get actionable intelligence about your security posture.
For the full technical details on how ThreatScore calculates your security posture, including formulas, weight assignment strategies, and pillar-specific scoring, check the docs: Prowler ThreatScore Documentation
Try it now in cloud.prowler.com



.avif)

.avif)












