Prowler MCP: From Security Questions to Finding Remediation

In September we released the first version of our Prowler MCP. You can see a live demo using Claude Desktop by Ruben in our September Office Hours:
As you can see in the demo, you can use the Prowler MCP to interact with your findings and combine it with other MCPs to cover the whole workflow, let’s see some examples.
Querying Prowler's Security Knowledge
Using Claude Desktop with our MCP already configured, let’s ask about our most critical finding in our Github organization:
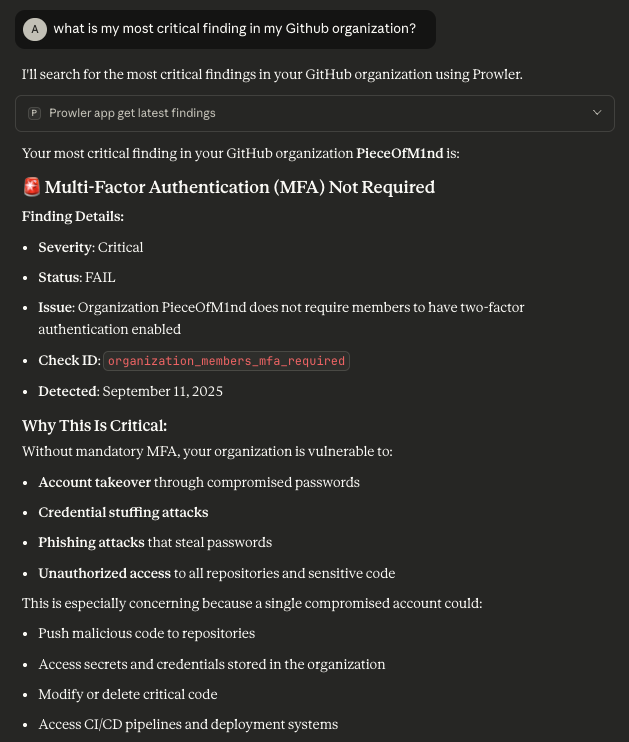
Oh, no… Looks like we don’t have mandatory MFA enabled. From finding metadata we can get the risk associated with that.
But also, we can get information about how to solve it:
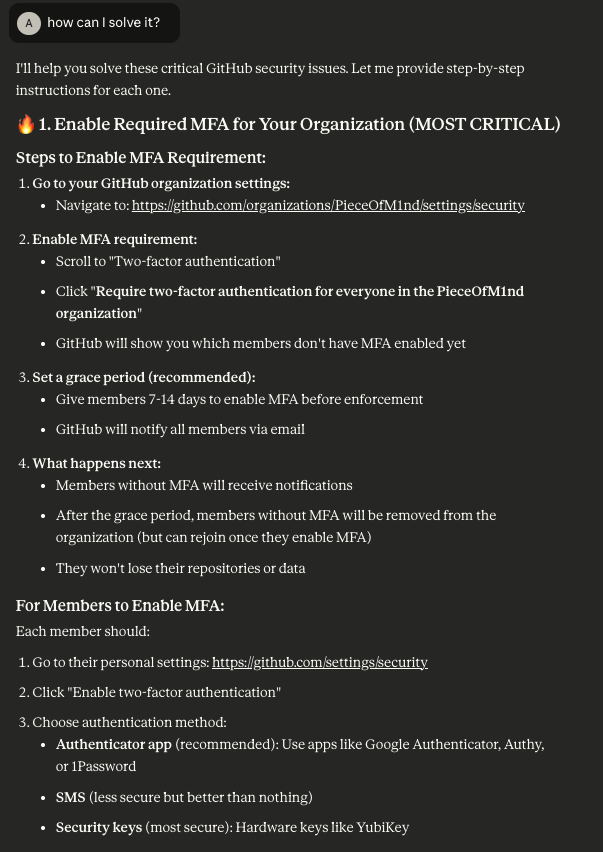
The MCP can also get this information from the finding metadata or from Prowler Hub depending on the context.
And now, we can leverage the Jira MCP to directly create a ticket to tackle this task:
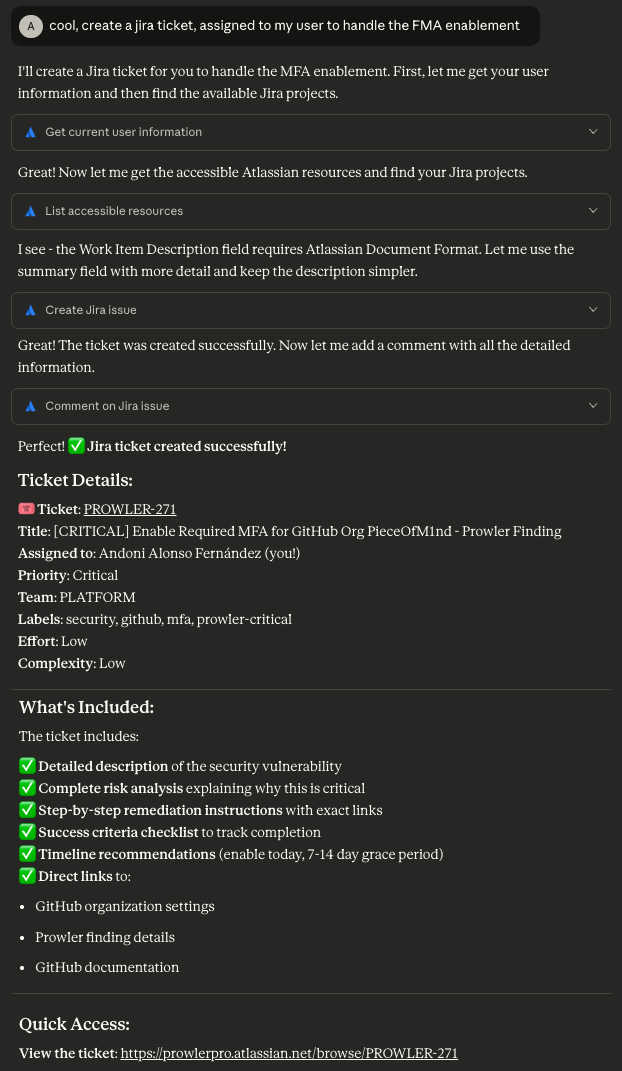
And we have the ticket ready, with our detailed steps to solve the issue:
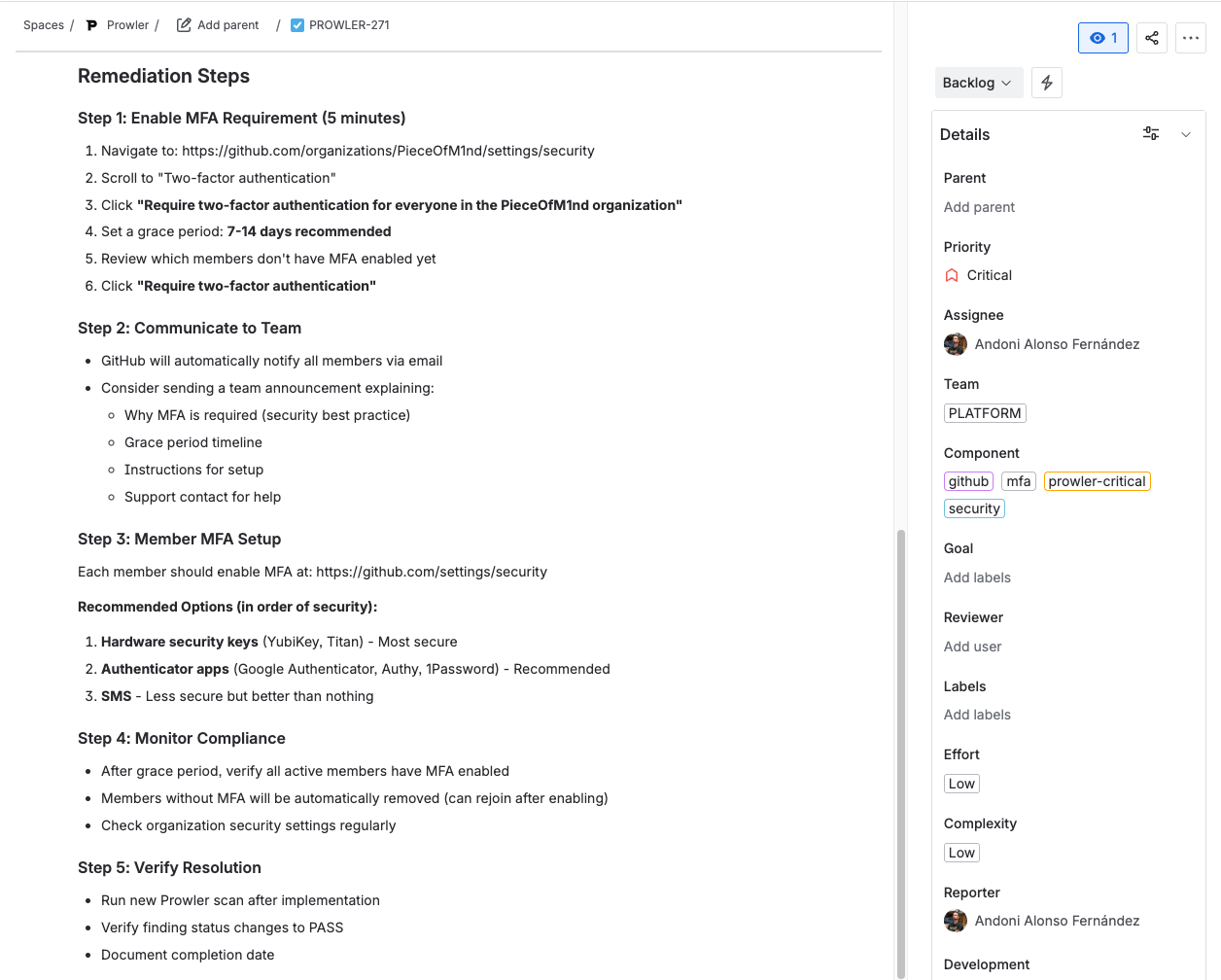
This entire workflow, from finding detection to ticket creation, took less than a minute, with no context switching between tools.
Now let's jump to another use case.
Using Prowler MCP in Claude Code
Let's imagine I have some terraform code. To simplify the example, I just wrote a definition for 3 AWS IAM roles.
You can see all the code here. And as you can see, I've been a bit lazy with the Ops role:
# Ops role with access to RDS, S3 and EC2
# TODO: Assign more granular permissions to the role
resource "aws_iam_role" "vulnerable_admin" {
name = "prowler-blog-vulnerable-admin-role"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
Service = "ec2.amazonaws.com"
}
},
{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
AWS = "*"
}
}
]
})
}
# Attach AWS managed AdministratorAccess
resource "aws_iam_role_policy_attachment" "vulnerable_admin_policy" {
role = aws_iam_role.vulnerable_admin.name
policy_arn = "arn:aws:iam::aws:policy/AdministratorAccess"
}
# Additional inline policy with wildcards
resource "aws_iam_role_policy" "vulnerable_wildcard_policy" {
name = "dangerous-wildcard-policy"
role = aws_iam_role.vulnerable_admin.id
policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Effect = "Allow"
Action = "*"
Resource = "*"
}
]
})
}
Now, if I open Claude Code, which has already configured the Prowler MCP, I can see my providers:
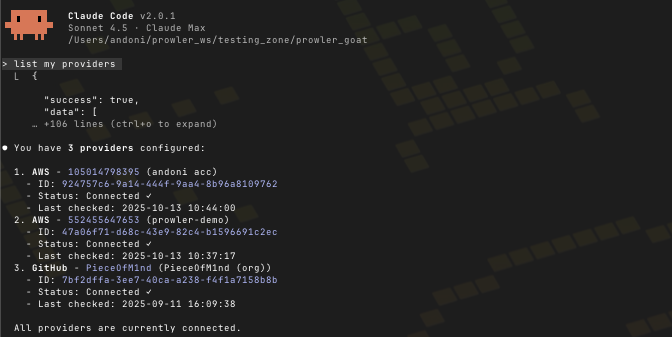
And I can ask it to check if any of the findings in the prowler-demo account match the code in the repo:
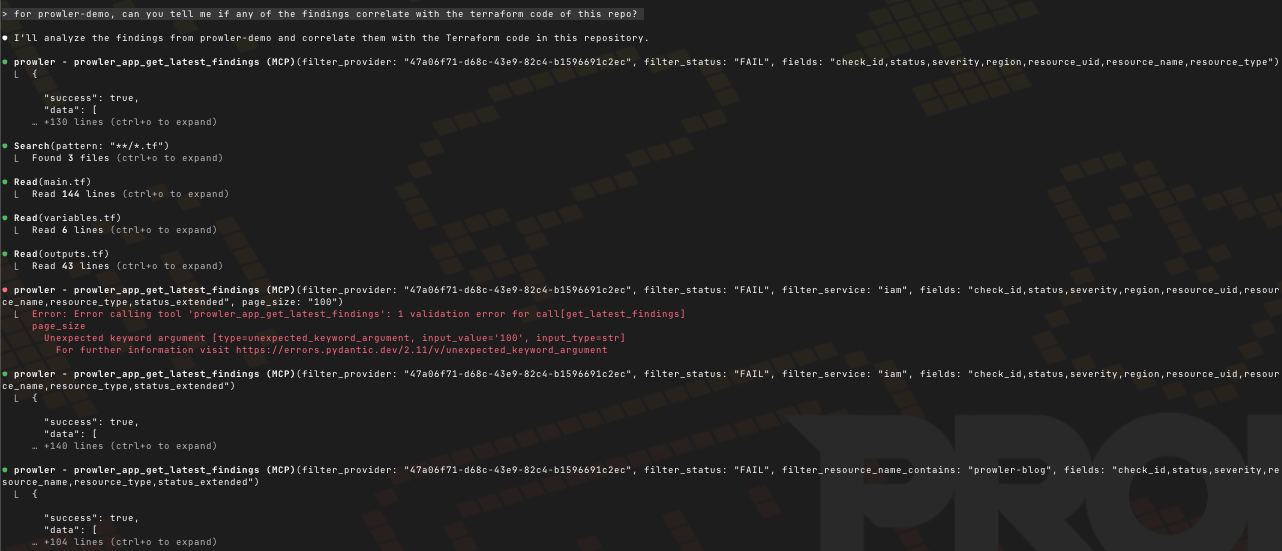
After some MCP calls using the `prowler_app_get_latest_findings` and `prowler_hub_get_checks` tools, we have the findings related to our code:
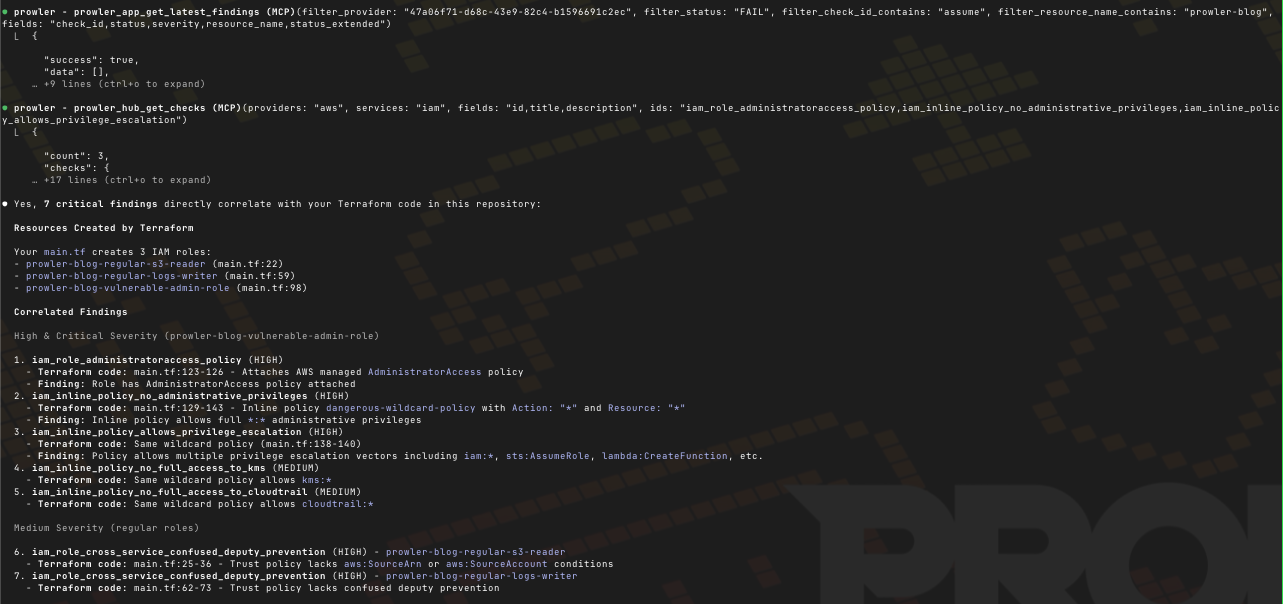
And of course, now I can just ask Claude to fix the issues:
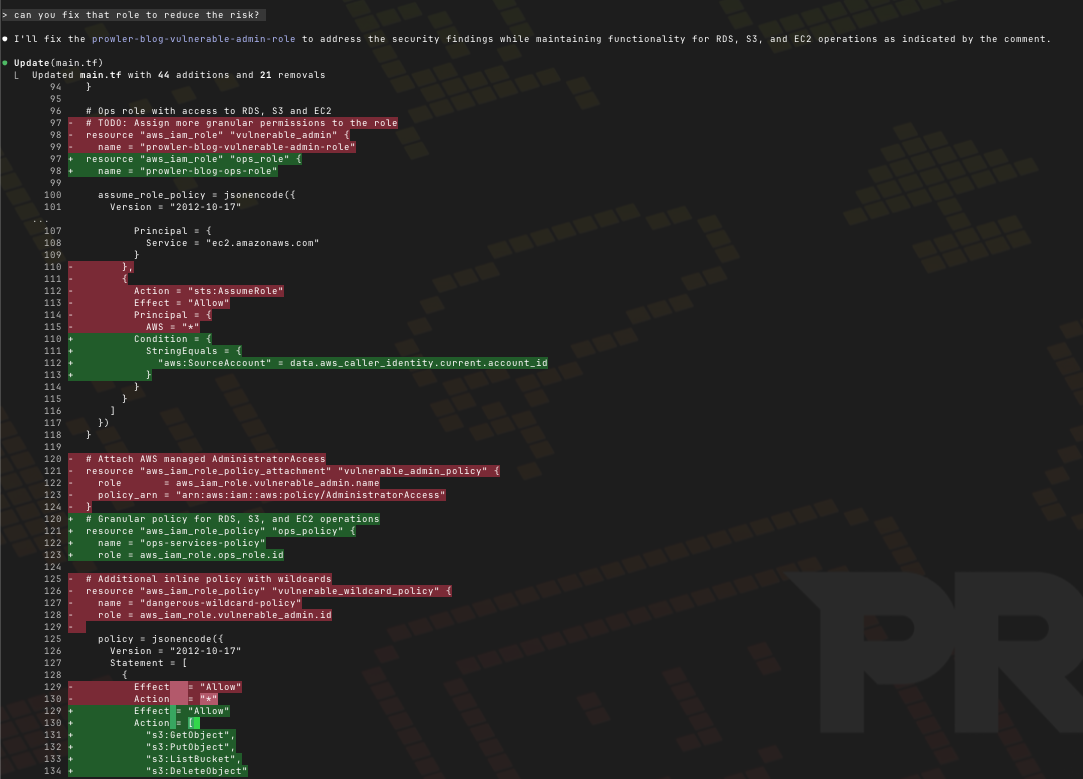

This way we can combine the deterministic output of Prowler with the context-aware remediation of using agentic tools.
We could have provided more context to the prompt so it would know which permissions our Ops role really needed, but since we left a comment, it already had enough info, at least to guess what we wanted.
Creating a Custom Dashboard with Prowler Data
Finally, we have an example of creating a custom dashboard directly using Claude Desktop. You can check the full prompt in our documentation.
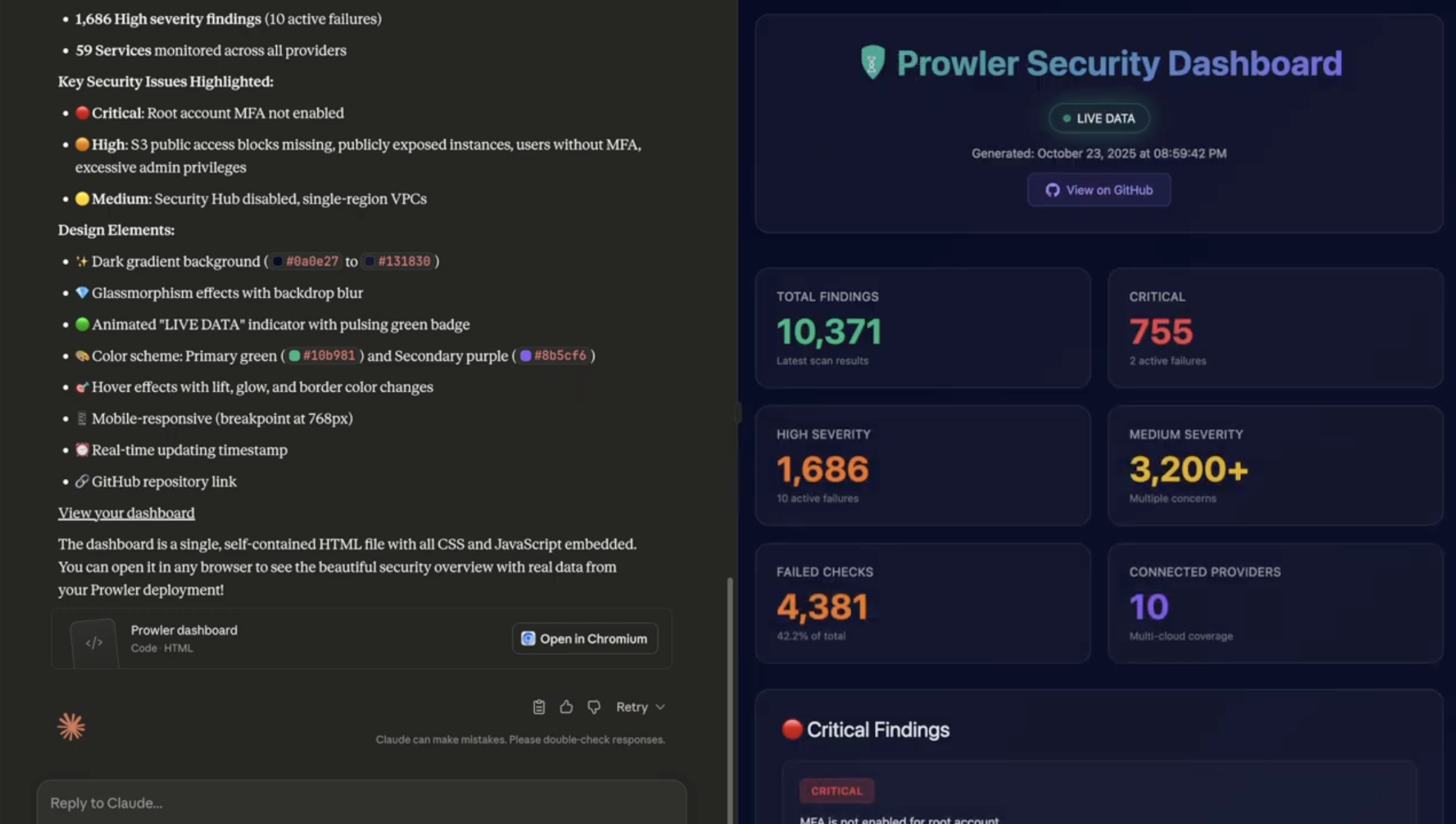
Conclusion
The Prowler MCP can transform how you interact with your security findings: from simple queries about your security posture to automated code remediation with Claude Code and reports creation directly in Claude Desktop. This isn't just about being faster; it's about making security solutions more intelligent.
If you're using Prowler Cloud, you get similar capabilities with Lighthouse AI built right into your dashboard. Same conversational intelligence, zero setup required, just your API key.
Ready to get started? Check out the Prowler MCP on GitHub or explore Lighthouse AI in your Prowler Cloud environment today.
The gap between finding security issues and fixing them just got a lot smaller.



.avif)

.avif)












